8 steps for implementing a successful print security plan
January 23, 2017
Channel, Security, Managed Print Services, Article, Trends
Amidst the proliferation of Internet of Things (IoT) endpoints, the cybersecurity threat landscape has expanded to every mobile, smart and cloud-enabled device on the network. This threatens the resilience of organisations not only from the disruption of business operations, but also the potential ramifications of a data breach can lead to financial loss, brand and reputational damage and loss credibility in the market place. Printers and multifunction printers (MFPs) are not immune to the security threat and are vulnerable to the same risks as any device on the network. As IoT devices they are susceptible to the growing threat of DDoS attacks – left unsecured they are an open door to the corporate network.
Quocirca’s latest report “Print security: An imperative in the IoT era” discusses the many points of vulnerabilities around print. With advanced connectivity and capacity to collect, process and store large volumes of data, the multifunction printer (MFP) has long been a ‘weak link’ in the IT infrastructure – one that businesses can no longer afford to be complacent about. In Quocirca’s survey, 61% of large enterprises admitted suffering at least one data breach through insecure printing.
Consequently, businesses must take a proactive and multifaceted approach to print security. This requires a full security evaluation of the print environment which can recommend the appropriate technology – including hardware and software security – as well as end-user education on responsible and secure printing practices.
Quocirca recommends that the following measures are taken:
- Ensure print devices are part of an overall information security strategy. Printers are no longer dumb peripherals and must be integrated into an organisation’s security policies and procedures.
- Adopt a security policy for the entire printer fleet. In the event of a data breach, an organisation must be able to demonstrate that it has taken measures to protect all networked devices. An organisation should be able to monitor, manage and report on the entire fleet, regardless of model, age or brand.
- Secure access to the network. Like other networked devices, MFPs require controls that limit network access, manage the use of network protocols and ports, and prevent potential viruses and malware.
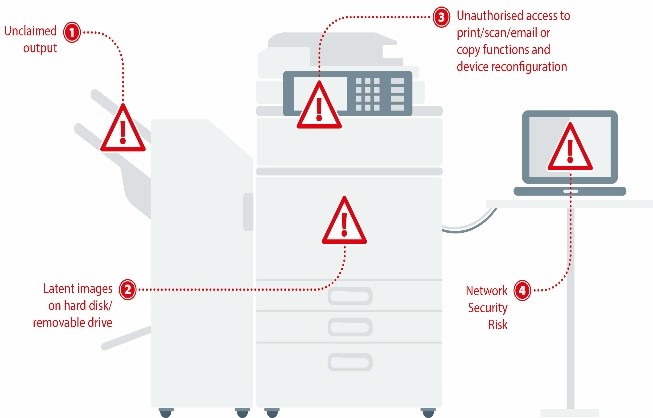
- Secure the device. Hard disk encryption adds an additional layer of security; securing stored data be it actively in use by the device, sitting idle on a device, and/or used by the device in a previous job. To avoid the risk of data being recovered when the MFP is moved or disposed of, data overwrite kits should be employed to remove all scan, print, copy and fax data stored in the hard disk drive.
- Secure access. Implement user authentication to eliminate the risk of unclaimed output being left in printer trays. User authentication, also known as pull printing, ensures documents are only released to the authorised recipient.
- Secure the document. In addition to access and device controls, digital rights management capabilities can further discourage unauthorised copying or transmission of sensitive or confidential information. This can be achieved by enabling features such as secure watermarking, digital signatures or PDF encryption.
- Ongoing monitoring and management. To ensure compliance and to trace unauthorised access, organisations need a centralised and flexible way to monitor usage across all print devices. Auditing tools should therefore be able to track usage at the document and user level. This can be achieved by either using MFP audit log data or third-party tools, which provide a full audit trail that logs the identity of each user, the time of use and details of the specific functions that were performed.
- Seek expert guidance. Manufacturers and Managed Print Service (MPS) providers continue to develop and enhance their security products and services. Take advantage of security assessment services which evaluate potential vulnerabilities in the print infrastructure. Note that not all assessments are equal. Ensure that the assessment provider demonstrates the credentials to fully evaluate the security risks across device, data and users. There are also a range of security certifications that are published by the National Institute for Standards and Technology.
Ultimately, print security demands a comprehensive approach that includes education, policy and technology. In today’s compliance driven environment where the cost of a single data breach can run into millions, organisations must proactively embrace this challenge. By using the appropriate level of security for their business needs, an organisation can ensure that its most valuable asset – corporate and customer data – is protected.
Read Quocirca’s Print Security: An Imperative in the IoT Era
You have Successfully Subscribed!
Stay ahead with industry insights
Receive Quocirca’s latest articles and research updates